Marc-Oliver Pahl (Professor, Chairholder)
Contact
Like all chair members, you reach me at surname@this domain.
Email policy
I receive a lot of email per day. Therefore, unluckily I cannot read all of them. If you do not receive an answer within 2 days, please feel free to recontact me as it is likely that I did not see your email.
Availability
You can see my current availability here.
Attention: do not consider any appointment confirmed where you did not receive a calendar invite from me.
About me
[starbox id=5]
My research
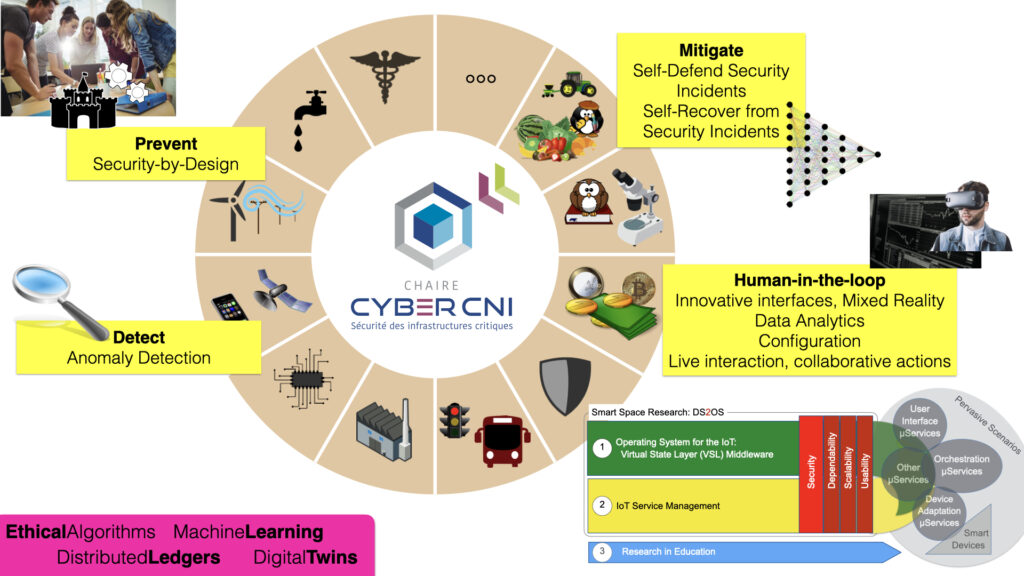
My research domain is cybersecurity. I follow a holistic multi-disciplinary approach, including the areas security-by-design, continuous monitoring and data analytics for anomaly detection, (semi-) automated defence for increasing resilience, and human-in-the-loop with multi-modal 3D interfaces.
Some keywords are: cybersecurity, security-by-design, digital twins, anomaly detection, semantics, microservices, middleware, access control, authentication, authorization, certificate-based security, end-to-end security, secure middle, peer-to-peer.
My publications
[tpcloud author=52,40,4]
My students
I am continuously supervising students since 2008. I supervised more than 150 Master- and Bachelor theses, 5 PhD theses at Tu Munich, and 6 PhD theses at IMT Atlantique.
[starbox id=am,ll,nd,ms,mf,ad,jb,ak,jb,lw,cl,ek desc=”Click on the name for more info…” orderby=display_name order=ASC]
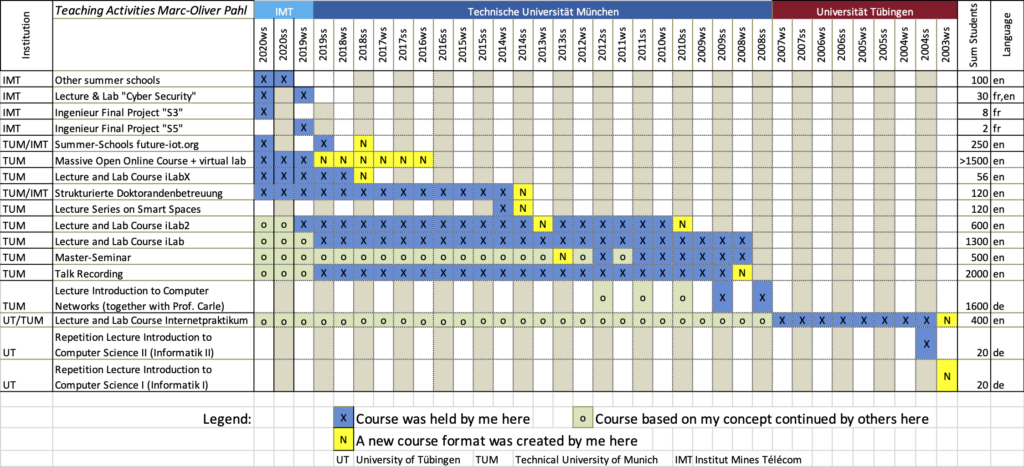
My teaching
I am teaching continuously at universities since 2003. I received multiple awards for my teaching including the 2013 Ernst Otto Fischer teaching award for excellent teaching and the 2020 supervisory award for excellent PhD supervision, both from Technical University of Munich.
Lighthouse activities are:
- The conception, creation, and operation of the biggest computer networks and distributed systems hands-on class series in Germany, the iLab, more at https://ilab.ilabxp.com/
- The MOOC iLabX – The Internet Masterclass https://ilabx.ilabxp.com/
- The PhD school series Future-IoT: IoT meets… More at https://future-iot.org/
The following table gives an overview on my teaching activities:
Current Positions
- Full Professor (2019-) Directeur de Recherches Grande Ecole (Technical University) Institut Mines Télécom
(IMT) Atlantique (prior Ecole nationale supérieure des télécommunications de Bretagne) / Department SRCD / Chaire Cyber CNI, Rennes, France - Chairholder of the Chaire Cybersecurity for Critical Networked Infrastructures (Cyber CNI) (1/2020-)
- – 8 professors
- – 1 engineer
- – 3 post-docs
- – 11 PhDs
- – 5industrypartners(Airbus,Amossys,BNPParibas,EDF, Nokia Bell Labs)
- – 2 regional partners (Région Bretagne, Pôle d’Excellence Cyber)
- Previously Co-Director of the multi-institute research team(UMR6285) LAB-STICC/IRIS (Sécurité et Résilience des Systèmes d’Information) (1/2020-2/2021) – 14 professors
– 1 research position – 1 technician
– 11 post-docs
– 22 PhDs - Member of the Steering Committee of the German-French Academy for the industry of the future (GFA) (2019-)
- Coordinator“FutureEducation” of the German-French Academy for the Industry of the Future (GFA) (2017-)
- Adjunct Professor, Carleton University, Canada (2019-)
- Vice-President, German Chapter of the ACM (2020-)
Previous Academic Position
- 2014-2020 Head of the IoT Smartspace Research Team at the Chair for Network Architectures and Services at Technical University of Munich, Germany – 5 PhD students and more than 200 Master, Bachelor and Diploma students under my supervision. – ProLehre Media and Didactics / External lecturer
- 2016-2017 Advisor of the Board of the Munich Center for Internet Research (MCIR), preparation of the transition to the current Bavarian Institute of Digital Transformation (BIDT)
- 2008-2014 Researcher and Lecturer at the Technical University of Munich
- 2005 External consultant for the interactive learning DVD “Netzwerktechnik” and Trainer at German “Berufsschulen”
Awards
- Supervisory Award for excellent PhD supervision (Technical University of Munich, Germany, 2020)
- Ernst Otto Fischer Lehrpreis (outstanding teaching award) (Technical University of Munich, Germany, 2013)
- Excellent teaching award (Technical University of Munich, 2018)
- Excellent teaching award (Technical University of Munich, 2016)
- Excellent teaching award (Technical University of Munich, 2015)
- Excellent teaching award (Technical University of Munich, 2014)
- Fellowship of the Klaus Tschira Foundation for the Heidel- berg Laureate Forum (2016)
Education
- 2018 Zertifikat Hochschullehre der Bayerischen Universitäten – Vertiefungsstufe (highest teaching certificate of Bavaria)
- 2014 PhD (Summa cum Laude), Technical University of Munich, “Distributed Smart Space Orchestration,” Focus on Internet of Things, Advisors: Prof. Dr.-Ing. Georg Carle, Munich; Prof. Gudrun Klinker, PhD, Munich
- 2008 Diploma (1.0 (best possible grade)), Eberhard Karls Universität Tübingen, “spy360.net — Webcampanoramen bis 360 Grad in HDR,” Focus on Image Processing, Advisors: Prof. Dr. Andreas Schilling, Tübingen; Prof. Dr. Dr. h.c. Wolfgang Straßer, Tübingen
Languages
- German (mother tongue): fluent
- English (working language): fluent
- French (working language): fluent
- Latin (“Großes Latinum”)
Memberships
- Association for Computing Machinery (ACM)
- German Chapter of the ACM (GChACM) – Vice-President (2020-2023; 2 terms)
- Institute of Electrical and Electronics Engineers (IEEE) – IEEE-IES Technical Committee on Factory Automation
- German Society for Informatics (GI)
- Deutscher Hochschullehrerverband (DHV)
Invited Talks
- “, “ AI for industry summer school, 2021
- Young Security Conference (YSC) 2021
- “CollaborativeRemoteSituationalCybersecurityAwareness,” SNCF Cyber Fusion Center, 2021
- “A holistic Approach to Cybersecurity, “ New Brunswick Cybersummit, 2021
- “IoT meets Security, “ 3rd Future-IoT PhD school, 2020
- “When data is the new oil, it is our role to prevent the blowout!, “ AI for industry summer school, 2020
- “When COVID-19 brings out the fundamentals of Artificial Intelligence, ” Atos Popup College, 2020
- “When Data is the New Oil, Security is the Blowout Preventer, ” IDSA VIRTUAL EXPO “Scaling in Europe with Data Sovereignty – a French Perspective”, 2020
- “IoT Smart Environment Research Vision, ” IMT Atlantique Séminaire au Vert, Département SRCD, Carnac, France, 2019 ̈
- “Ziemlich beste Freunde? Uber die Vereinbarkeit von Digitaler Transformation und Privatsphäre” (Pretty much best friends? On the compatibility of digital transformation and privacy), German Informatics Society, Munich, Germany, 2019
- “Privacy or why should I care? Security and Privacy aspects of Autonomous Driving,” Autonomous Vehicle Safety and Security meetup, Munich, Germany, 2019
- “Cross-layer optimization for time- and security-critical IoT applications,” Huawei, San Jose, USA, 2019
- “Composing the (Industrial) Internet of Things(IIoT),”Siemens CKI Forum, Munich, Germany, 2019
- “Taming the Internet of Things: DS2OS – a secure data- centric service-oriented approach,” Arctic University (Randi Karlson), Tromsø, Norway, 2019
- “Securing the Internet of Things – Because it is Your Data!,” Data61/ CSIRO (Ingo Weber), Sydney, Australia, 2018
- “The Future of Teaching? How Combining Online and Of- fline Learning can become the Key,” University of Sydney (Ralph Holz), Sydney, Australia, 2018
- “Securing the Internet of Things,” keynote at the AdHoc Now conference (Nicolas Montavont), St. Malo, France, 2018
- “The iLab Concept – Making Teaching better, at Scale,” Ja- cobs University Bremen (Jürgen Schönwälder), Bremen, Ger- many, 2018
- “Smart Space Orchestration – How to make the Internet of Things smart?”, Eurecom (Jérome Härri), Sophia Antipolis, France, 2016
- “Datenzentrierte Modulare Gebäudeautomatisierung im Internet der Dinge,” (Datacentric Modular Building Automation
in the Internet of Things), keynote at the IT4ENERGY-Workshop 2015 – Dezentrale Energiesysteme in der Gebäude- und Wohnungswirtschaft (Armin Wolf), Berlin, Germany, 2015 - “ServiceorientierteArchitektureninBaaS,”(Service-Oriented Architectures in BaaS), keynote at the IT4ENERGY-Workshop 2014 – Gebäudewirtschaft und Energienetze (Thomas Luckenbach), Berlin, Germany, 2014
- “The iLab experience – a blended learning hands-on course concept,” keynote at the EU Tempus Event for the Modernisation of Higher Education (Helmut Seidl), Munich, Germany, 2013
Raised Funding
I am constantly mounting projects with a volume for my groups of over 2 000 000 EUR (in overall projects of several 10 MEUR) until 2021. I am experienced in the national and international public and private funding acquisition sectors. From the beginning, I am often in leading roles in projects. The funding covers research and teaching activities.
Project Coordination
- 2018-2021 BMBF/ Business Finland (DE, FI) Decentralized Cross-commodity Energy Management (DECENT): Overall coordinator DE consortium, PI TUM
- 2013-2016 BMBF / ITEA (DE, ES, TR) Building as a Service (BaaS): Technical Coordinator, PI TUM
- 2008-2011 BMBF / CELTIC (DE, FR, SE) Autonomic Home Networking (Authone): Technical Project Lead TUM
- Lead author of numerous national and international proposals that unluckily did not get funded.
Community Service
- Publication co-chair, ACM/ IEEE/ IFIP Network Operations and Service Managment (NOMS) 2022
- Experience Session Co-Chair of the IFIP/IEEE International Symposium on Integrated Network Management (IM) 2021
- Workshop Co-Chair ACM/ IEEE/ IFIP Network Operations and Service Managment (NOMS) 2020
- Student Travel Grant Chair ACM/ IEEE/ IFIP International Conference on Network and Service Management (CNSM) 2019
- Associate Editor ACM International Journal of Network Ma- nagement (IJNM) (2018-)
- Guest Editor Special Issue Wiley’s Internet Technology Let- ters (with Michel Barbeau (Carlton University, Canada; Joaquin, IMT Sud Paris, France) 2019
- General Co-Chair of the IFIP / IEEE Decentralized Orchestration and Management of Distributed Heterogeneous Things (DOMINOS) Workshop 2018, 2019
- TPC Co-Chair Global Information Infrastructure and Net- working Symposium (GIIS) 2019, IEEE International Conference on Ad Hoc Networks and Wireless (Adhoc-Now) 2018
- Panel Co-Chair of the IFIP/IEEE International Symposium on Integrated Network Management (IM) 2019
- Demo Co-Chair IFIP / IEEE Cloudification of the Internet of Things (CIoT) 2018
- Organizer IFIP / IEEE HOT topics in Network and Service Management (HOTNSM) 2019
- Organizer IFIP / IEEE Distributed Orchestration and Management of Distributed Heterogeneous Things (DOMINOS) 2018
My review activity
I am in the OC of multiple conferences, mainly in the network service and management community.
Conferences
To be filled
- 2022-01 CIoT
- 2021-12 ICC
Journals
- 2022-01 TNSM
