At the IRISA SOTERN 2025 cybersecurity seminar, the CNI Cyber Chair presented its innovations in honeypots and strategies against digital disinformation, reinforcing cybersecurity research.
Disinformation driven by generative artificial intelligence poses new challenges for cybersecurity, society, and regulation. This Europe-wide research project, led by the Cyber CNI Chair in collaboration with Frankfurt University of Applied Sciences and IMT Atlantique, invites experts to share their insights through a short academic survey.
La désinformation alimentée par l’intelligence artificielle générative représente un enjeu majeur pour la société et la cybersécurité. Dans le cadre d’un projet de recherche à l’échelle européenne, la Chaire Cyber CNI lance une enquête et invite les experts à partager leur expérience. Ce travail est mené conjointement par l’IMT Atlantique (Marc-Oliver Pahl, Elie Chedemail) et la Frankfurt University of Applied Sciences (Martin Kappes, Alexander Loth).
Le 12 mai 2025, la 8ᵉ édition de l’atelier Manage-IoT s’est tenue à Honolulu, lors du symposium IEEE/IFIP NOMS 2025. Cet événement a réuni des experts autour de la gestion des réseaux et des systèmes IoT. Les discussions ont porté sur la gestion à base d’intentions, la sécurisation des systèmes IoT hétérogènes et l’Industrie 5.0. Découvrez les moments clés de cette rencontre et son lien avec les travaux de la chaire.
On Wed, Jan 11th, 2023, 2pm CET, Guillaume Neau (AWS, FR), will talk about “Securing the Cloud: Encryption and Data Protection“. You are cordially invited to join the free live stream on youtube and LinkedIn! Please share the link https://talk.cybercni.fr/26
On Wed, Dec 7th, 2022, 2pm CET, Cristian Hesselman (SIDN Labs, NL), will talk about “Increasing Internet security by bridging research and operations“.
Join the free youtube and LinkedIn live streams!
Please share the link https://talk.cybercni.fr/25
On Oct 17, 2022, our PhD student Hassan CHAITOU presented her latest results regarding “Optimization of security risk for learning on heterogeneous data“: https://youtu.be/BI4r3xikugI
Please help us spreading the news that the registration is open for our 5th Future-IoT.org PhD school on “IoT meets Automation” from Aug 29-Sep2, 2022 in Berlin: https://school.future-iot.org. Below you find the corresponding email. Please share it in your communities via mail, LinkedIN, etc. Looking forward to welcoming many of you and your students in Berlin!
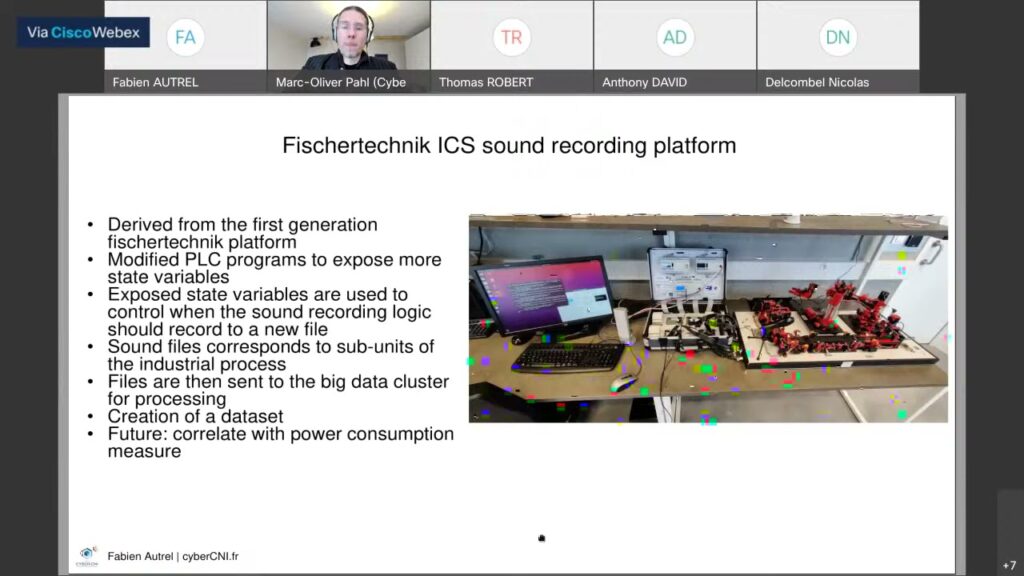
The cyberCNI.fr (https://cyberCNI.fr/) Research Update (Spring/ Fall) happens once per semester. It is the big status event of the chair Cyber CNI. All works around the chair are presenting their progress, current works, and next challenges. In this talk, our research engineer Fabien Autrel presents how we improved our testbed based on Fischertechnik and CyberRange technologies.
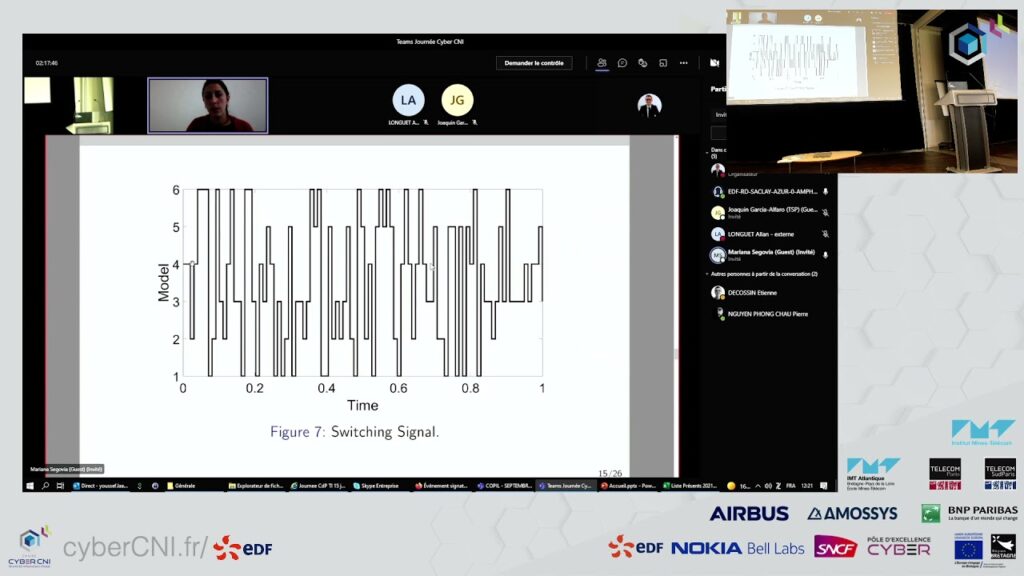
On Sep 21, 2021, we had the pleasure to visit our partner EDF in Paris Palaiseau. Today, Mariana present her work. In her talk, she will explain how to make control of cyber-physical systems resilent, using switched linear control system.




![[TALK26] Securing the Cloud: Encryption and Data Protection – Guillaume Neau (Amazon Web Services, FR)](https://cybercni.fr/wp-content/uploads/2023/01/talk.cybercni.fr_.speaker.slide_.002-2-1024x576.jpg)
![[TALK25] Increasing Internet security by bridging research and operations, Cristian Hesselman (SIDN Labs, NL)](https://cybercni.fr/wp-content/uploads/2022/12/TALK25-Increasing-Internet-security-by-bridging-research-and-operations-Cristian-Hesselman-1-1024x576.jpg)
![[RU2/22] Hassan CHAITOU : Optimization of security risk for learning on heterogeneous data](https://cybercni.fr/wp-content/uploads/2022/10/RU222-Hassan-CHAITOU-PhD-Student-Telecom-Paris-1024x576.jpg)