Europe’s cybersecurity and cyberdefense community met in Rennes for the 6th edition of the European Cyber Week (ECW) from Nov 16-18, 2021. Together with our chairholder Marc-Oliver Pahl, Léo Lavaur, Anthony David, and Nicolas Delcombel, three of our PhD students, presented a demo on our research line covering Virtual Reality interfaces for improving human-machine communication in cybersecurity.
On Feb 23, 2021, 5pm CET I Soumya Banerjee (TRASNA), will talk about “Securing the Internet of Things: Latice-based crypto and side-channel attacks“. Watch the trailer here: https://youtu.be/fPpLk3BpQjY?list=PLdftPKA9mTfaDJxqwexil2mPhUFIA9ITd
You are cordially invited to join the free live stream on youtube and LinkedIn! To register and subscribe to the series announcements, just enter your mail address in the box on the left at https://talk.cybercni.fr/. Please share the link https://talk.cybercni.fr/2022-02 with your interested friends!
Share and like: On Jan 25, 2021, 5pm CET I Carol Fung (Virginia Commonwealth University, US), will talk about “Security and Privacy Protection for IoT Networks“. Watch the trailer here.
You are cordially invited to join the free live stream on youtube and LinkedIn! To register and subscribe to the series announcements, just enter your mail address in the box on the left at https://talk.cybercni.fr/. Please share the link https://talk.cybercni.fr/2022-01 with your interested friends!
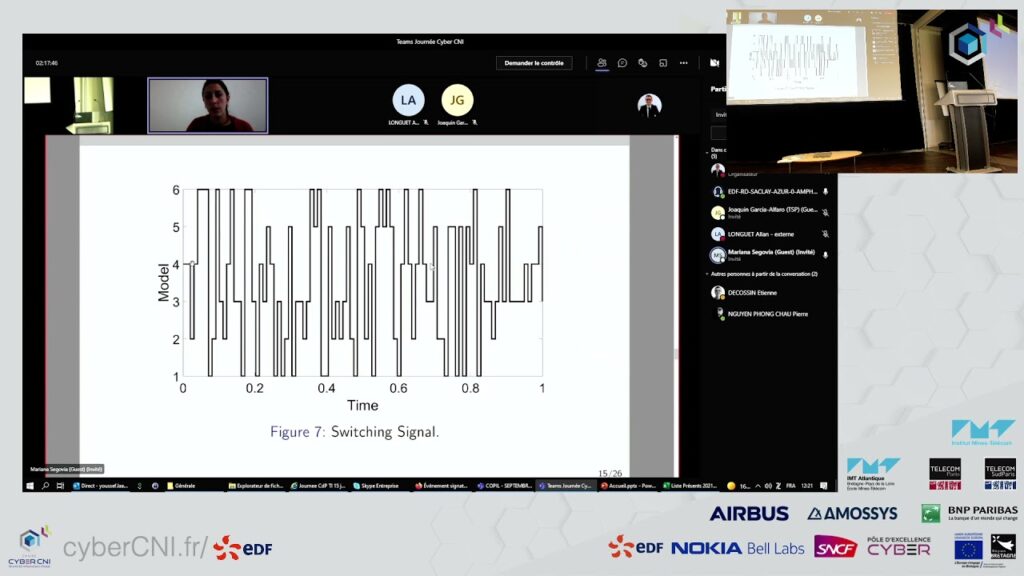
On Sep 21, 2021, we had the pleasure to visit our partner EDF in Paris Palaiseau. Today, Mariana present her work. In her talk, she will explain how to make control of cyber-physical systems resilent, using switched linear control system.
The chair is also active in teaching. The final year student project “Autoprotection : éthique VS agents autonomes et algorithmes” looks at an important aspect of our technology-dependent world: ethical aspects of autonomous functionality. Good examples are self-driving / autonomous cars, building automation, or production sites. Maintaining and increasing cybersecurity are a key goals for autonomous functionality. Enjoy the video of the intermediate presentation with the current results! (in French)
On Sep 21, 2021, we had the pleasure to visit our partner EDF in Paris Palaiseau! Here is another highlight presentation:
Hassan CHAITOU, Security risk optimization for learning on heterogeneous quality data
A classifier is a component used in the automation of “decision-making” or complex data abstraction: intruder detection, speed limitation extraction. For an efficient classifier, the training must be on a large volume of data and be renewed over time by integrating or revoking certain learning data. From a security point of view, this process represents a risk since it offers the attacker various ways of degrading classifier performance (either by forcing classifications mischievous, either by randomly degrading its performance). These two types of attacks require more or less effort from the attacker.
This risk is exacerbated when data comes from sources (network equipment, organizations) corresponding to heterogeneous trust levels. Hassan’s thesis aims at controlling the risk associated with this update via game theory in the case where the confidence in the learning data is not homogeneous.
On Sep 21, 2021, we had the pleasure to visit our partner EDF in Paris Palaiseau! Here is another highlight presentation:
Julius BÜNGER, Keeping software in massive IoT installations up-to-date
Julius’s thesis will provide solutions to ease the IoT device recycling. An object may become unusable for several reasons, for example a hardware failure, no more energy from the battery or obsolete functions. In that case, it is important to decommission the device, and recycle it. One solution for recycling is to re-use the object in a different application or deployment, if it embeds the necessary functions. It can also be disassembled and its parts can be sent to different recycling industry. In order to make this possible, we need to address the issues of localization, keep-alive,classification and security.
Dear members and friends of the chair CyberCNI.fr, we wish you all the best for the year 2022! May many of your wishes become reality! Click on the video to watch our wishes….